Cyberly
Weapons-grade security arsenal for startups against cyber threats
What is Cyberly? Complete Overview
Cyberly provides a comprehensive security arsenal designed to protect startups from advanced cyber threats. Unlike traditional security measures, Cyberly simulates real-world attacks to identify vulnerabilities before they can be exploited. The tool focuses on multiple attack vectors including networks, data, mobile apps, web applications, APIs, and cryptographic systems. By proactively identifying and addressing security flaws, Cyberly helps startups safeguard their valuation and reputation. The target audience includes startups, SaaS companies, e-commerce platforms, and any business reliant on digital infrastructure.
Cyberly Interface & Screenshots
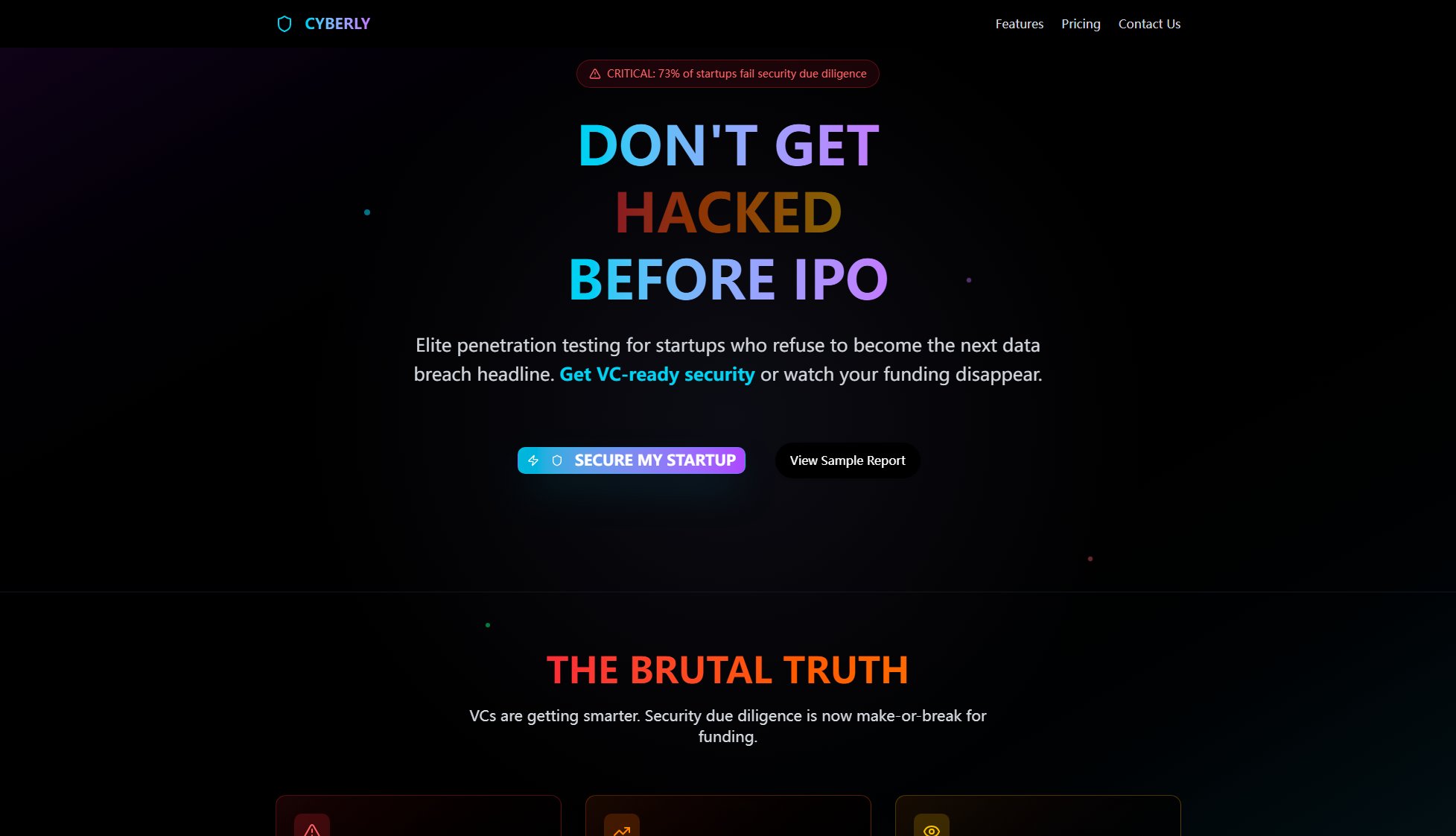
Cyberly Official screenshot of the tool interface
What Can Cyberly Do? Key Features
Network Infiltration
Cyberly conducts advanced network penetration testing to simulate real attacker tactics. This includes bypassing firewalls, lateral movement within networks, and compromising internal systems. The tool tests VPNs, WiFi, and other perimeter defenses to identify weaknesses and provide actionable fixes.
Data Extraction
This feature focuses on database security assessments. Cyberly attacks databases directly using techniques like injection, privilege escalation, and misconfiguration exploits. It identifies exfiltration paths to ensure sensitive customer data remains secure.
Mobile Destruction
Cyberly performs thorough security testing for iOS and Android apps. It decompiles apps, hooks into their processes, and uses fuzzing techniques to uncover vulnerabilities such as hidden API keys, weak encryption, and unsafe data storage practices.
Web Annihilation
Full-stack web application testing that mimics real attacker behavior. Cyberly identifies vulnerabilities like XSS, CSRF, and business logic flaws across frontend and backend systems. It supports SaaS, e-commerce, and web portals.
API Exploitation
Cyberly tests REST and GraphQL APIs for security flaws including rate-limit bypasses, authentication issues, injection vulnerabilities, and privilege escalation. It ensures APIs don't leak sensitive data fields.
Crypto Breaking
This feature audits encryption and authentication systems. Cyberly tests password hashing, token security, and secret storage methods. It identifies weak cryptographic implementations that could undermine customer trust.
Best Cyberly Use Cases & Applications
Startup Security Audit
A tech startup preparing for Series A funding uses Cyberly to identify and fix security vulnerabilities that could impact their valuation. The comprehensive testing reveals critical flaws in their API implementation that could have led to data breaches.
E-commerce Platform Protection
An e-commerce platform employs Cyberly to test their web application and payment systems before a major sales event. The testing uncovers several business logic flaws that could have allowed price manipulation and order fraud.
Mobile Banking App Security
A fintech company uses Cyberly's mobile testing capabilities to assess their banking app's security. The assessment reveals insecure data storage practices that could have compromised sensitive financial information.
How to Use Cyberly: Step-by-Step Guide
Contact Cyberly through their website to discuss your security needs and schedule an assessment.
Provide necessary access to your systems, networks, or applications that need testing.
Cyberly's team performs comprehensive penetration testing across all specified vectors.
Receive detailed reports documenting all vulnerabilities found and their potential impact.
Work with Cyberly's experts to implement fixes and hardening measures for identified vulnerabilities.
Optional: Schedule follow-up tests to verify the effectiveness of implemented security measures.
Cyberly Pros and Cons: Honest Review
Pros
Considerations
Is Cyberly Worth It? FAQ & Reviews
Cyberly is ideal for startups, SaaS companies, e-commerce platforms, fintech firms, and any business that handles sensitive data or relies on digital infrastructure for operations.
Assessment duration varies based on scope, but most single-vector tests take 1-2 weeks, while comprehensive assessments may require 3-4 weeks.
Yes, our Enterprise Security Program includes documentation to support compliance with standards like SOC2, ISO 27001, and PCI DSS.
Yes, we provide detailed remediation guidance and can work directly with your team to implement fixes, especially with our Comprehensive and Enterprise packages.
We recommend quarterly testing for most companies, or continuous testing for high-risk environments through our Enterprise program.