Gecko Security
AI-powered security that understands your codebase
What is Gecko Security? Complete Overview
Gecko Security is an advanced AI-powered security tool designed to identify business logic flaws and multi-step vulnerabilities that traditional SAST tools often miss. Unlike conventional scanners that rely on pattern matching, Gecko builds a semantic understanding of your application by analyzing code paths, developer intent, and infrastructure context. This approach significantly reduces noise and false positives while uncovering complex security risks. The tool is particularly effective for modern development teams working with microservices and dynamically typed languages. Gecko has already demonstrated its capabilities by discovering 30+ 0-day vulnerabilities in popular open-source projects. It serves a wide range of users from individual developers to large enterprises, offering different pricing tiers to accommodate various team sizes and security needs.
Gecko Security Interface & Screenshots
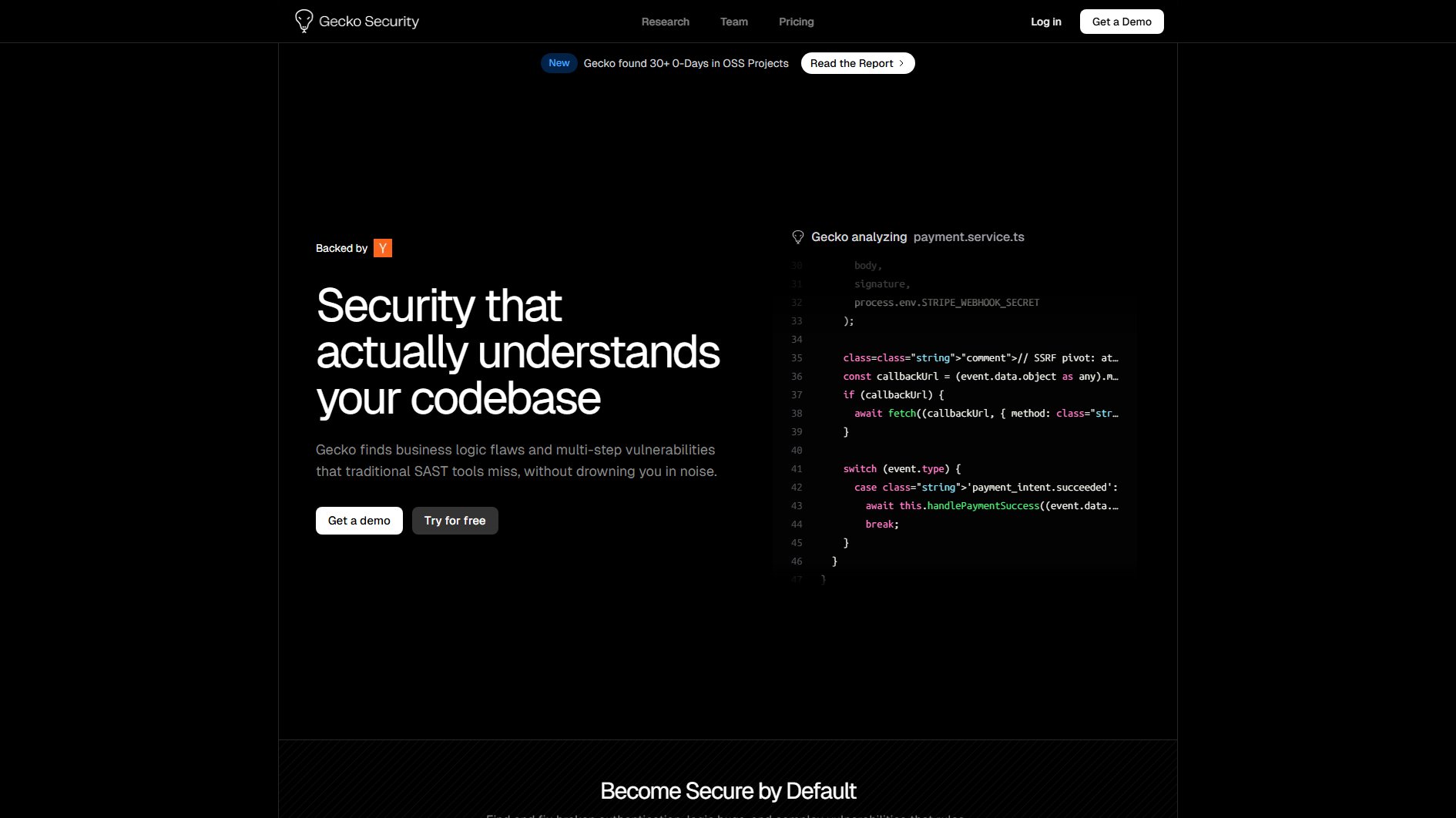
Gecko Security Official screenshot of the tool interface
What Can Gecko Security Do? Key Features
Semantic Code Analysis
Gecko goes beyond traditional AST parsing by using semantic name bindings similar to language server protocols. This allows it to truly understand the meaning of your code, making it particularly effective for microservice architectures and dynamically typed languages. The analysis maintains context across your entire codebase, infrastructure, and documentation to identify subtle security issues.
Business Logic Vulnerability Detection
The tool specializes in finding complex business logic flaws that rules-based scanners miss. By analyzing code paths and developer intent, Gecko can identify vulnerabilities in authentication flows, authorization checks, and data validation that could lead to security breaches.
Threat Modeling Automation
Gecko automates threat modeling by aligning it with your business and security objectives. It models targeted, exploitable attack paths based on your actual codebase, helping security teams focus on the most critical risks.
Low-Noise Prioritization
With a reported false positive rate of around 20%, Gecko significantly reduces triage time by focusing on remotely exploitable issues. Each finding comes enriched with context, proof-of-concepts, and actionable fixes.
Multi-Step Vulnerability Detection
The tool excels at identifying vulnerabilities that require multiple steps to exploit, which are often missed by traditional scanners. This includes complex authentication bypasses, privilege escalation chains, and data validation flaws.
Best Gecko Security Use Cases & Applications
Open Source Project Maintenance
Open source maintainers can use Gecko's free tier to scan their public repositories. The tool has already found critical vulnerabilities in popular OSS projects like BentoML and AutoGPT, helping maintainers secure their code before attackers exploit these issues.
Enterprise Application Security
Large organizations can deploy Gecko Enterprise to continuously monitor their entire codebase. The automated threat modeling and business logic analysis helps security teams keep pace with rapid development cycles while maintaining strong security standards.
CI/CD Pipeline Integration
Development teams can integrate Gecko into their CI/CD pipelines to automatically scan every pull request. The PR bot provides immediate feedback on security issues, preventing vulnerabilities from being merged into production code.
Security Research
Security researchers can leverage Gecko's advanced analysis capabilities to discover novel vulnerability patterns in complex applications. The tool's ability to trace data flows across microservices makes it particularly valuable for modern architectures.
How to Use Gecko Security: Step-by-Step Guide
Sign up for a free account or request a demo on the Gecko Security website. The onboarding process is straightforward, with options to connect your GitHub or other version control systems.
Configure your scan settings by selecting repositories to analyze. Gecko supports both public and private repositories, with different limits based on your pricing tier.
Initiate the scan. Gecko will analyze your codebase, building a semantic model that understands your application's architecture and data flows.
Review the findings in the dashboard. Vulnerabilities are prioritized by exploitability and impact, with detailed explanations and proof-of-concept examples.
Implement fixes using the provided remediation guidance. For Pro and Enterprise plans, you can integrate Gecko into your CI/CD pipeline to automatically scan pull requests.
Monitor your security posture over time with continuous scanning and threat modeling updates as your codebase evolves.
Gecko Security Pros and Cons: Honest Review
Pros
Considerations
Is Gecko Security Worth It? FAQ & Reviews
Gecko uses an AI native engine to build a semantic understanding of your application. It links together context from your code, infrastructure and documentation to trace how data flows and trust boundaries occur. By threat modelling targeted attack scenarios, Gecko surfaces multi step and business logic vulnerabilities that pattern matching tools overlook.
Rather than using brittle AST parsing or call graph analysis, Gecko relies on semantic name bindings similar to a language server protocol. This makes its analysis more accurate, especially for microservice architecture, because it truly understands the meaning of your code and can parse dynamically typed languages. This approach leads to a lower false positive rate, of around 20 per cent based on customer testimonials and industry benchmarks, and prioritisation of remotely exploitable issues.
Yes, Gecko is built for security-conscious enterprises and supports private AI models and self-hosted deployments, ensuring security vulnerability data and source code remain completely under your control.
Gecko specializes in analyzing modern web applications and supports popular languages like JavaScript/TypeScript, Python, and others. Its semantic analysis approach makes it particularly effective for dynamically typed languages.
Yes, the Pro plan offers a 7-day free trial, and the Basic plan is completely free for open source projects. You can also request a demo to see Gecko in action with your own codebase.