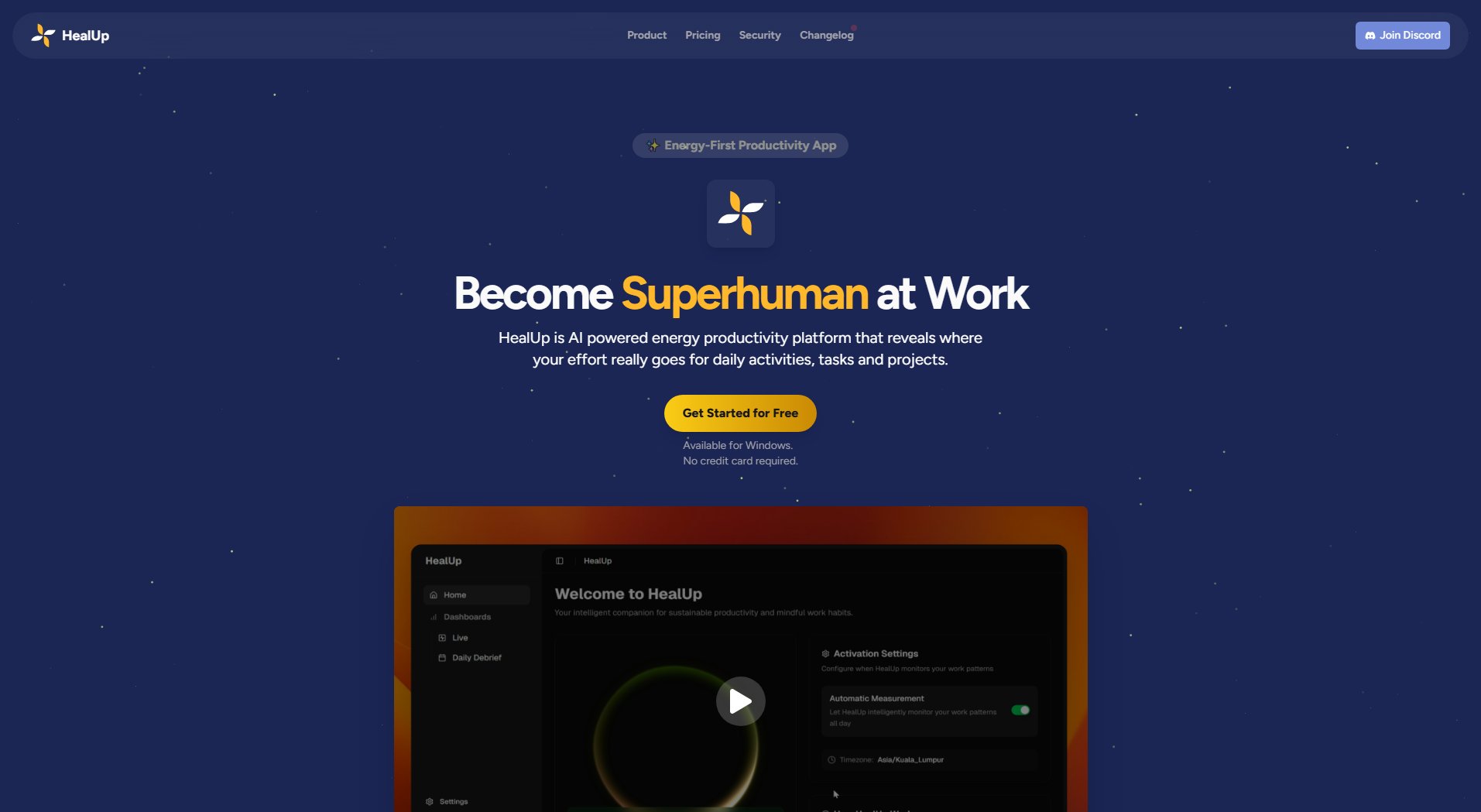
Ray Security
Predictive Data Security Platform for Smarter Enterprise Protection
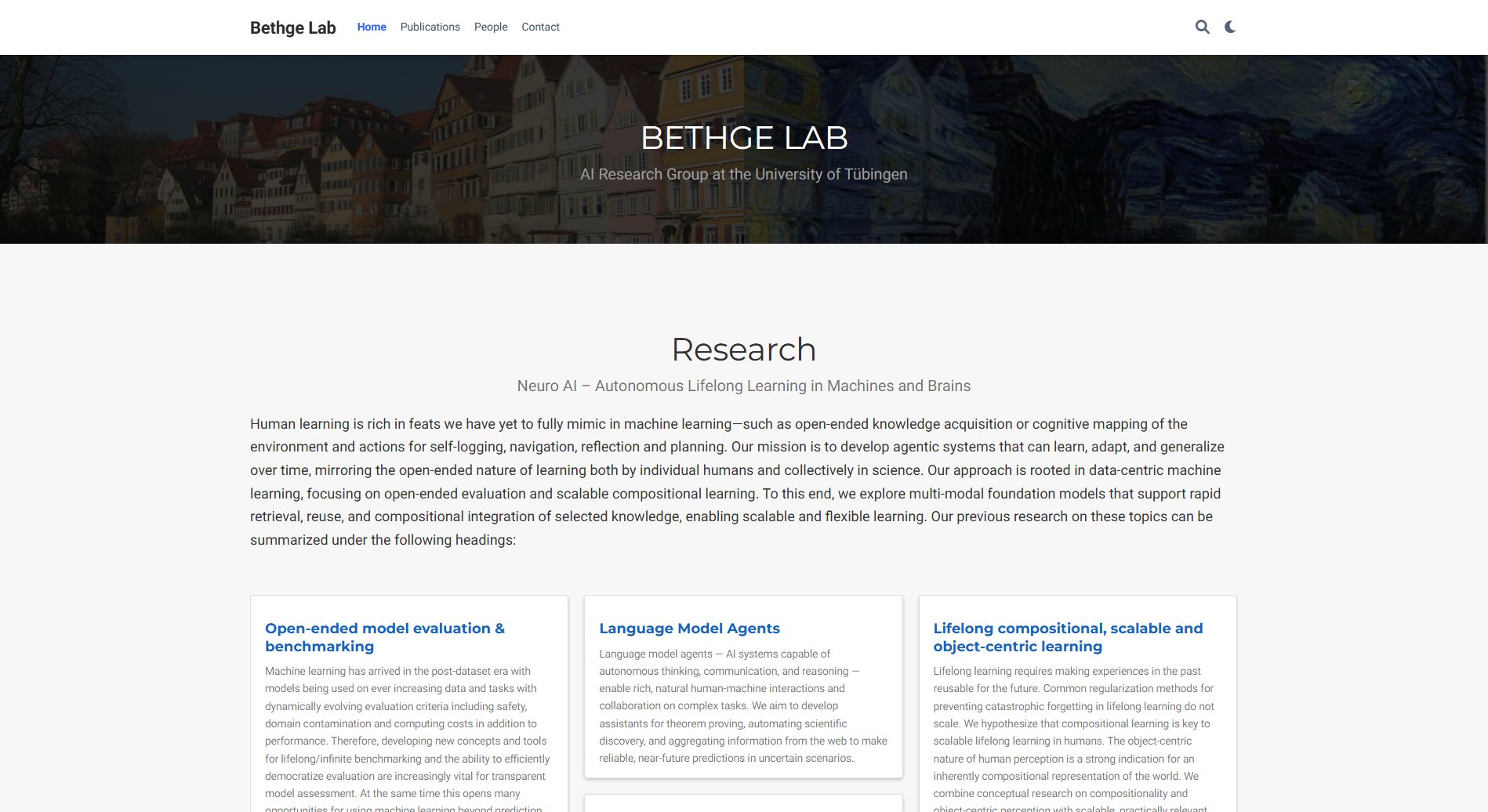
What is Ray Security? Complete Overview
Ray Security is the first predictive data security platform that transforms how enterprises protect their data. Unlike traditional solutions that treat all data equally, Ray Security leverages artificial intelligence to predict usage patterns, enabling smarter security for both used and unused data. This innovative approach addresses critical pain points such as inefficient data protection, high storage costs, and reactive threat responses. By focusing on actual data usage, Ray Security reduces the attack surface while maintaining business agility. The platform is designed for enterprises across industries, particularly those handling sensitive data, such as financial services, healthcare, and technology. With seamless integration, intelligent data management, and real-time threat adaptation, Ray Security empowers organizations to operate with confidence and significantly reduce risk.
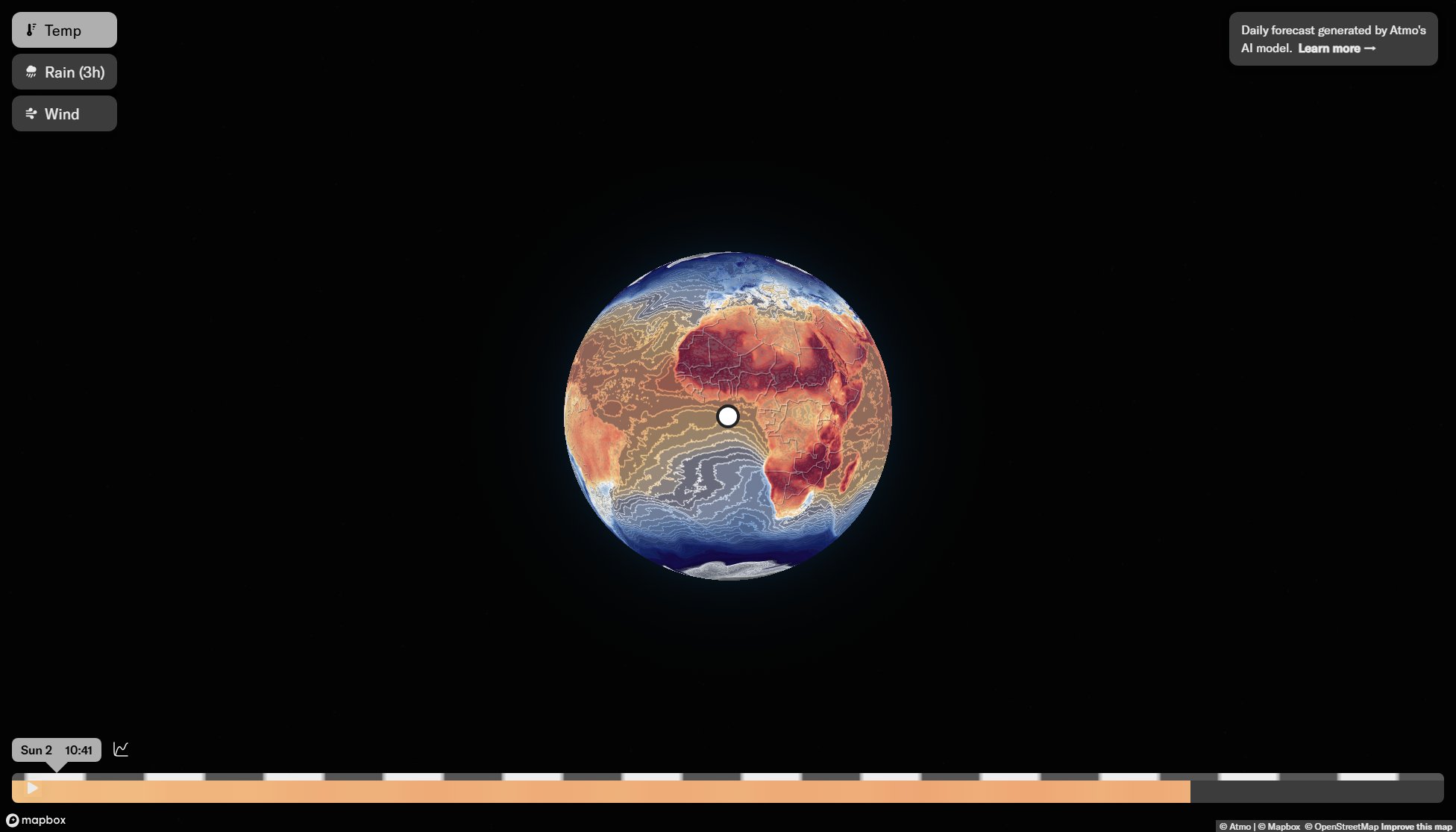
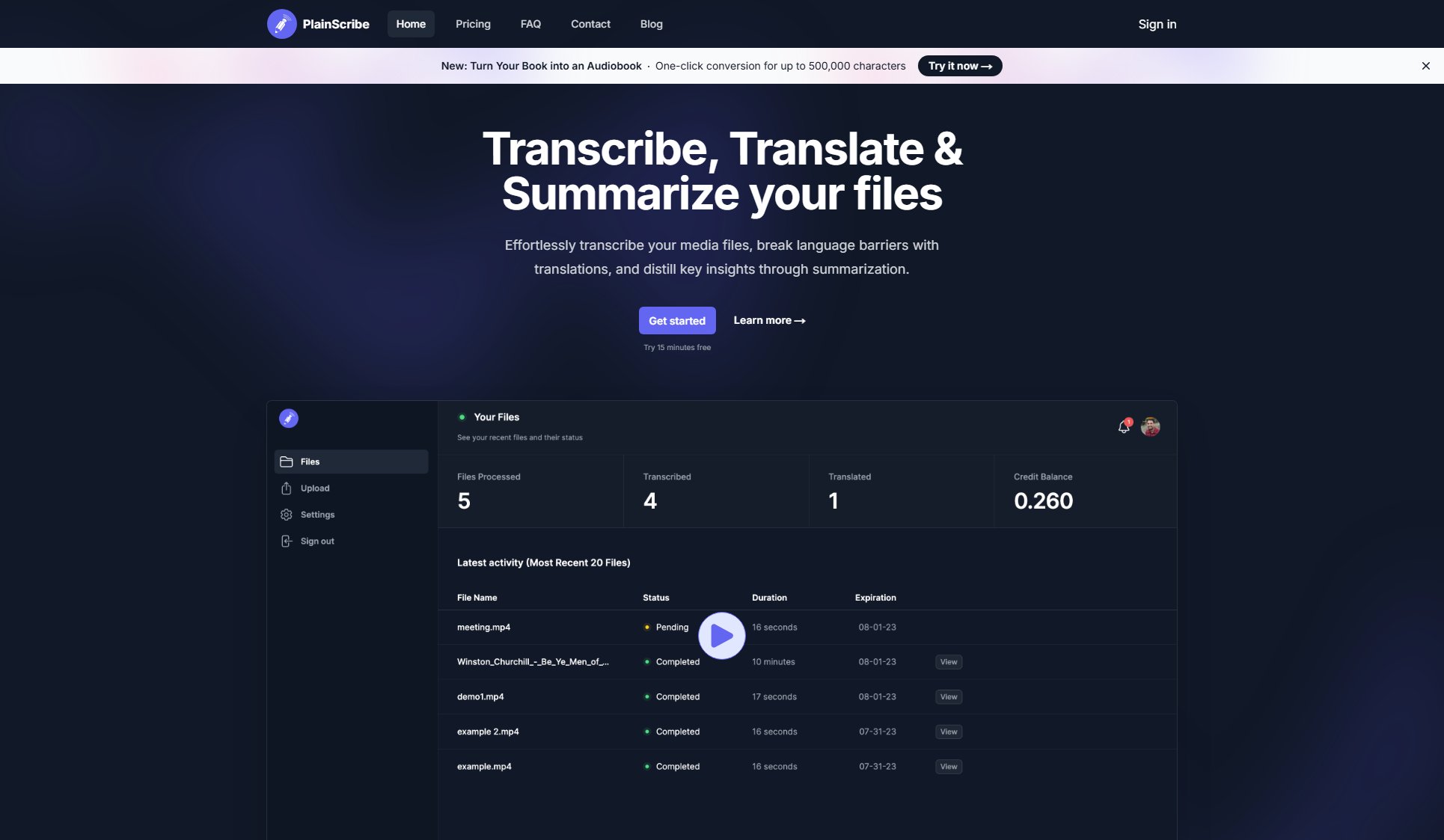
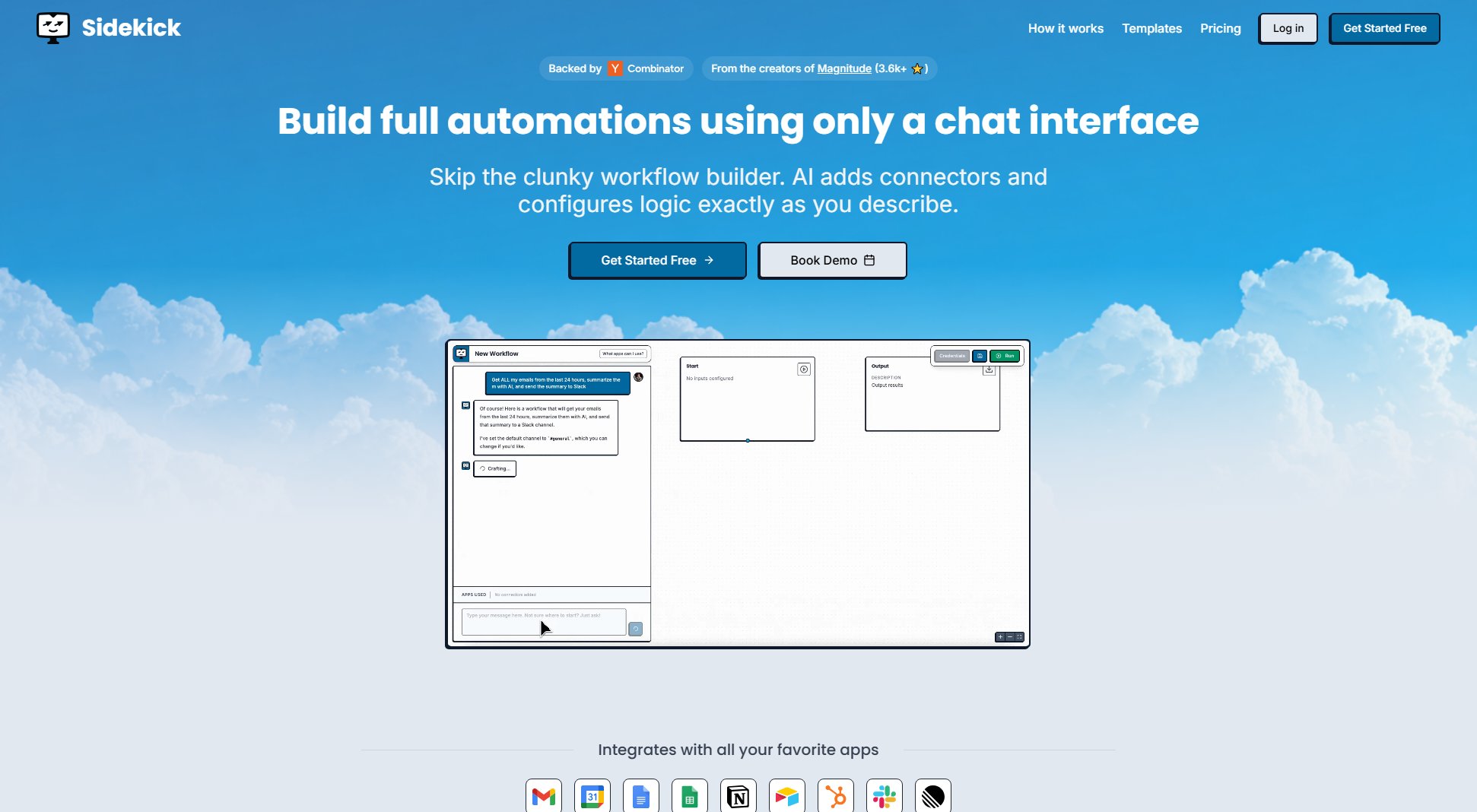
Ray Security Interface & Screenshots
Ray Security Official screenshot of the tool interface
What Can Ray Security Do? Key Features
Predictive Data Usage Analysis
Ray Security uses AI to predict how data will be used, allowing enterprises to apply security measures proactively. This reduces unnecessary protection on unused data while ensuring critical data is always secure.
Intelligent Data Management
The platform optimizes data movement and storage, significantly cutting costs by identifying and securing only the data that will be used. This feature is praised for its ability to streamline operations without compromising security.
Real-Time Threat Adaptation
Ray Security continuously monitors data usage patterns and adapts security protocols in real-time to mitigate emerging threats before they manifest, providing a dynamic defense mechanism.
Contextual, Risk-Based Access Controls
The platform enforces access controls based on contextual risk assessments, ensuring that only authorized users can access sensitive data under the right conditions, thereby minimizing exposure.
Seamless Integration
Ray Security is designed to integrate effortlessly with existing enterprise systems, offering robust data security without disrupting business workflows. Customers highlight the smooth and swift integration process.
Best Ray Security Use Cases & Applications
Financial Services Data Protection
A global bank uses Ray Security to predict and secure transactional data, reducing exposure to breaches while ensuring compliance with stringent financial regulations. The platform’s predictive capabilities help prioritize high-risk data, cutting storage costs by 30%.
Healthcare Data Optimization
A healthcare provider leverages Ray Security to manage patient records efficiently. By identifying rarely accessed data, the provider reduces storage overhead and enhances security for frequently used records, improving both cost-efficiency and patient privacy.
Enterprise Threat Prevention
A technology firm integrates Ray Security to adaptively protect intellectual property. The platform’s real-time threat adaptation prevents unauthorized access attempts, significantly lowering the risk of data leaks.
How to Use Ray Security: Step-by-Step Guide
Sign up for Ray Security and connect your enterprise data sources to the platform. The setup process is straightforward, with guided steps to ensure all data repositories are securely linked.
Configure your security preferences and risk thresholds. Ray Security provides customizable settings to align with your organization’s specific security policies and compliance requirements.
Allow the AI to analyze your data usage patterns. The platform will begin predicting which data is actively used and which remains dormant, optimizing security measures accordingly.
Monitor real-time insights and alerts. Ray Security’s dashboard offers a clear view of potential threats and adaptive security actions, enabling quick responses to any anomalies.
Review reports and adjust settings as needed. The platform provides detailed analytics on data usage, security incidents, and cost savings, helping you refine your strategy over time.
Ray Security Pros and Cons: Honest Review
Pros
Considerations
Is Ray Security Worth It? FAQ & Reviews
Ray Security uses AI to predict data usage patterns, allowing for proactive and adaptive security measures. Unlike traditional platforms, it focuses on securing data that will be used, reducing unnecessary protection and costs.
Yes, Ray Security is designed for seamless integration with a wide range of enterprise systems. Customers report swift and hassle-free integration processes.
Yes, Ray Security offers a Free plan with basic features. You can upgrade to paid plans for more advanced capabilities.
By identifying and securing only the data that will be used, Ray Security minimizes the need for extensive storage of unused data, leading to significant cost savings.
Enterprise customers receive 24/7 dedicated support, including custom integrations and priority assistance for any issues.