Commission Pilot Hub
Public-access project dashboard for streamlined management
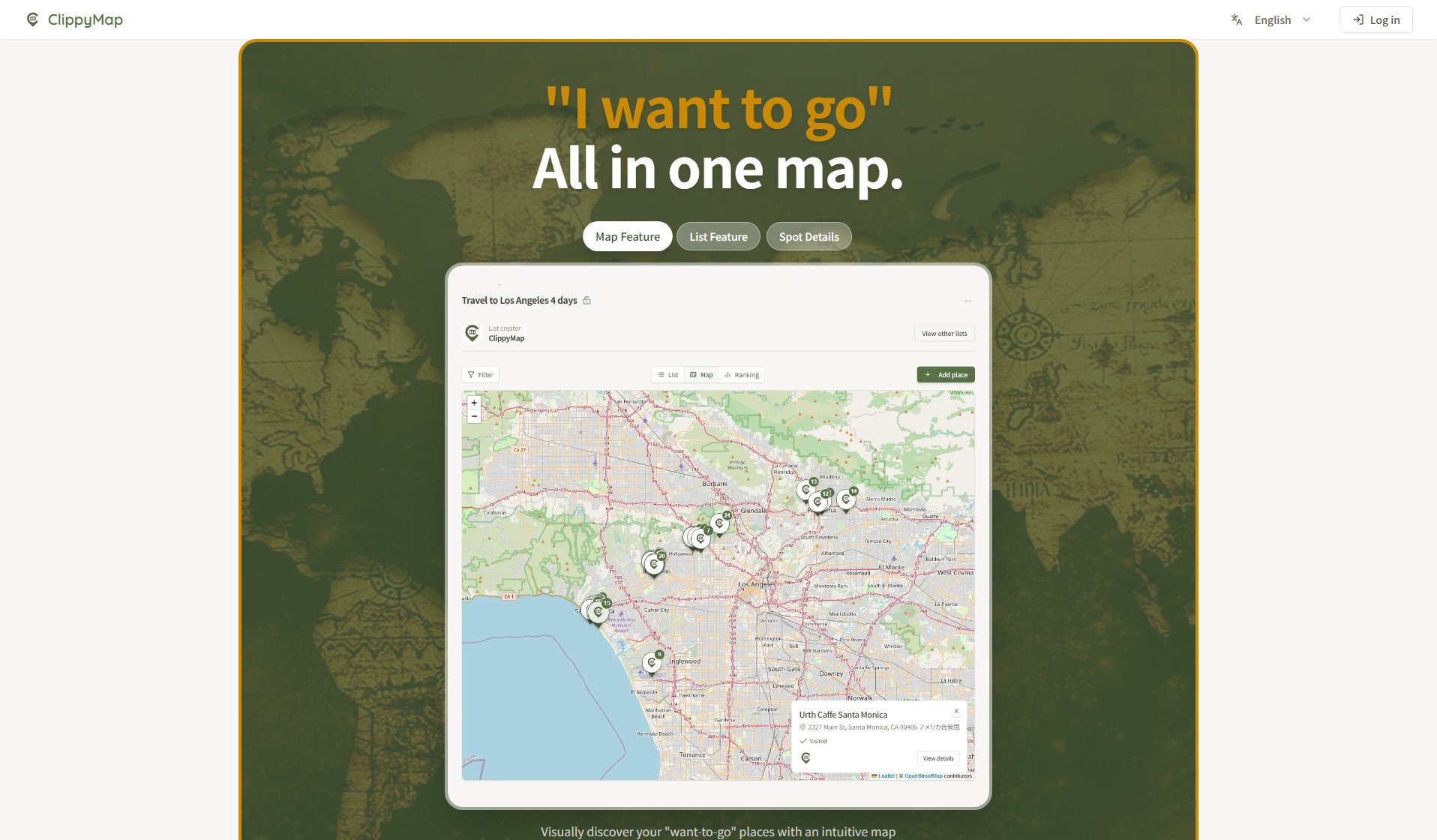
What is Commission Pilot Hub? Complete Overview
Commission Pilot Hub is an accessible project management dashboard that offers public access without strict authentication requirements. The tool allows users to enter any email and password combination to access project management features, making it ideal for quick collaboration and temporary access scenarios. It serves teams and individuals who need immediate access to project tools without complex setup processes. The platform simplifies project management by eliminating traditional login barriers while maintaining core functionality.
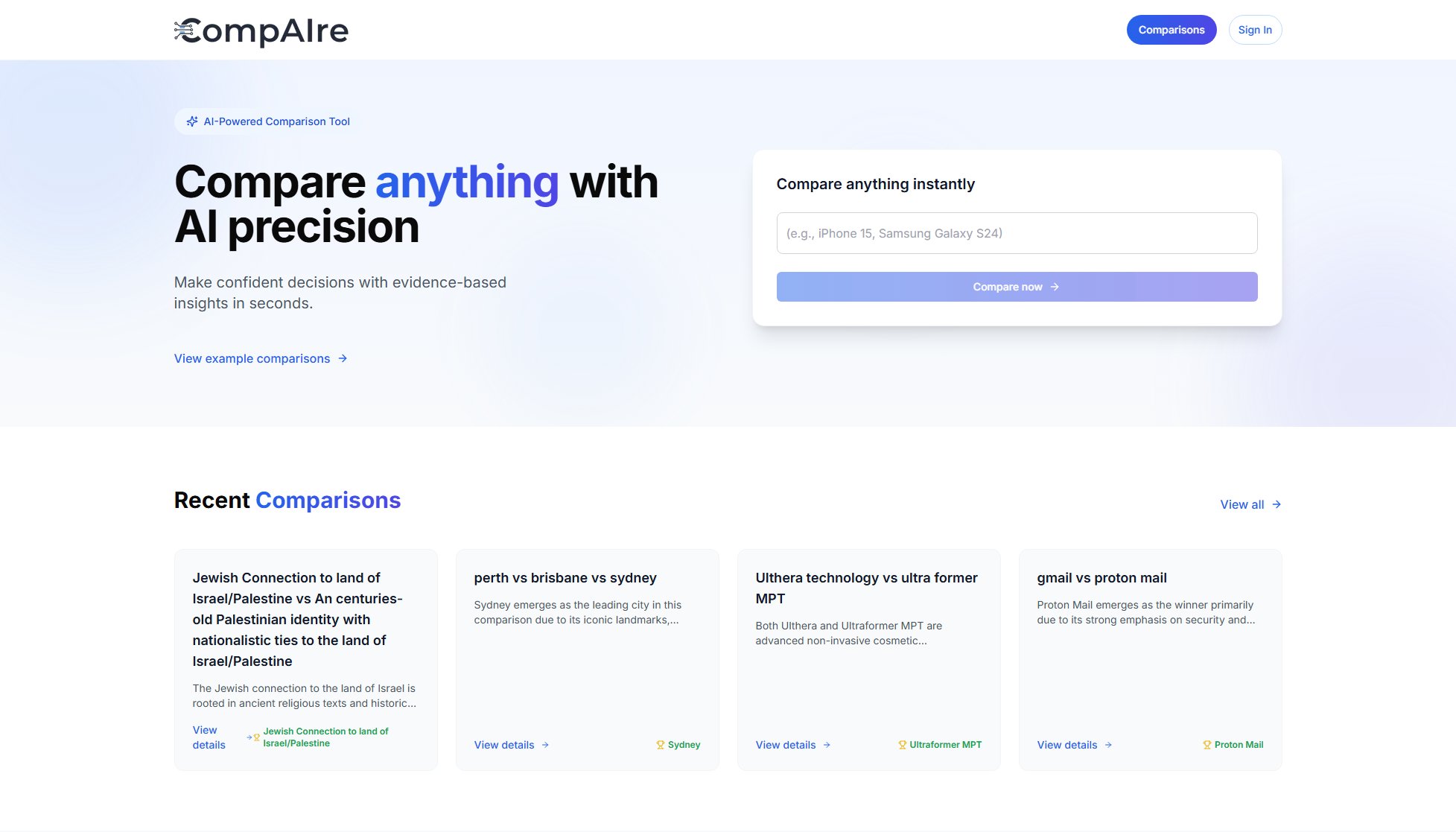
Commission Pilot Hub Interface & Screenshots
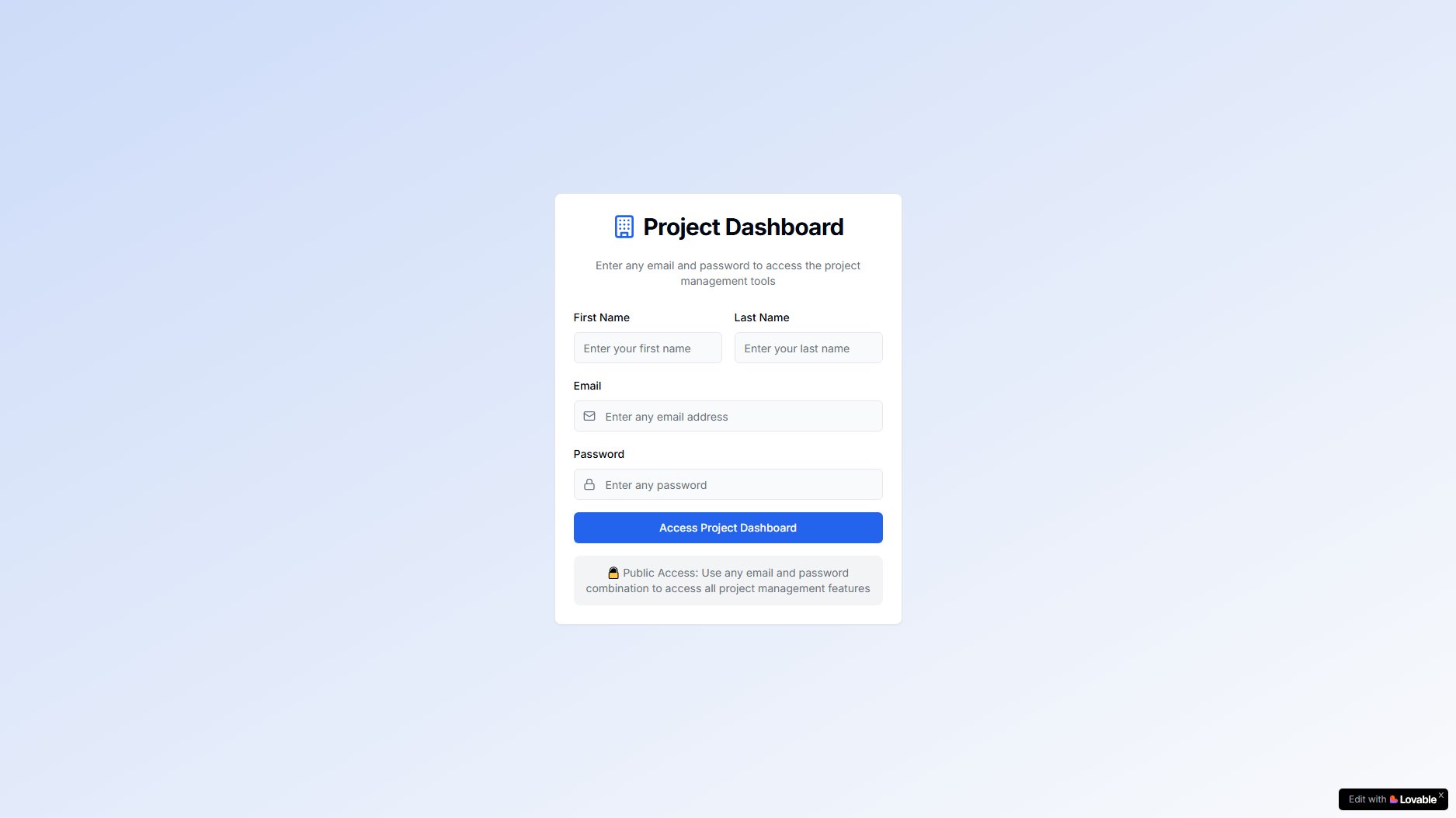
Commission Pilot Hub Official screenshot of the tool interface
What Can Commission Pilot Hub Do? Key Features
Public Access
Unique open-access system allows entry with any email/password combination, removing traditional authentication barriers for faster project access.
Project Dashboard
Centralized interface for managing all project components with intuitive controls and visualization tools.
Quick Setup
Immediate access without registration or verification processes enables instant project collaboration.
Best Commission Pilot Hub Use Cases & Applications
Temporary Team Collaboration
Facilitates quick onboarding of temporary team members who need immediate access to project tools without account setup.
Client Demonstrations
Allows agencies to quickly demonstrate project management features to potential clients without creating dedicated accounts.
How to Use Commission Pilot Hub: Step-by-Step Guide
Navigate to the Commission Pilot Hub website at baseopstech.app
Enter any email address (no verification required) in the email field
Create or enter any password combination
Click 'Access Project Dashboard' to immediately enter the management interface
Commission Pilot Hub Pros and Cons: Honest Review
Pros
Considerations
Is Commission Pilot Hub Worth It? FAQ & Reviews
The public access system is designed for convenience in non-sensitive environments. For confidential projects, additional security measures should be implemented.
The current implementation allows open access. For restricted access requirements, alternative authentication methods would need to be implemented.