ThreatOps
Advanced cyber threat intelligence platform with real-time AI-powered analysis
What is ThreatOps? Complete Overview
ThreatOps is a comprehensive cybersecurity solution providing advanced threat intelligence, security operations management, vulnerability management, and incident response capabilities. The platform aggregates real-time intelligence from trusted sources including MITRE ATT&CK, AlienVault OTX, and CISA KEV, enhanced with AI-powered analysis to detect and mitigate emerging threats. Designed for security professionals and enterprises, ThreatOps helps organizations stay ahead of sophisticated cyber attacks by providing actionable intelligence, indicators of compromise (IoCs), and mitigation strategies. The platform automatically updates threat data every 30 minutes, offering unparalleled visibility into global cyber threats across industries and regions.
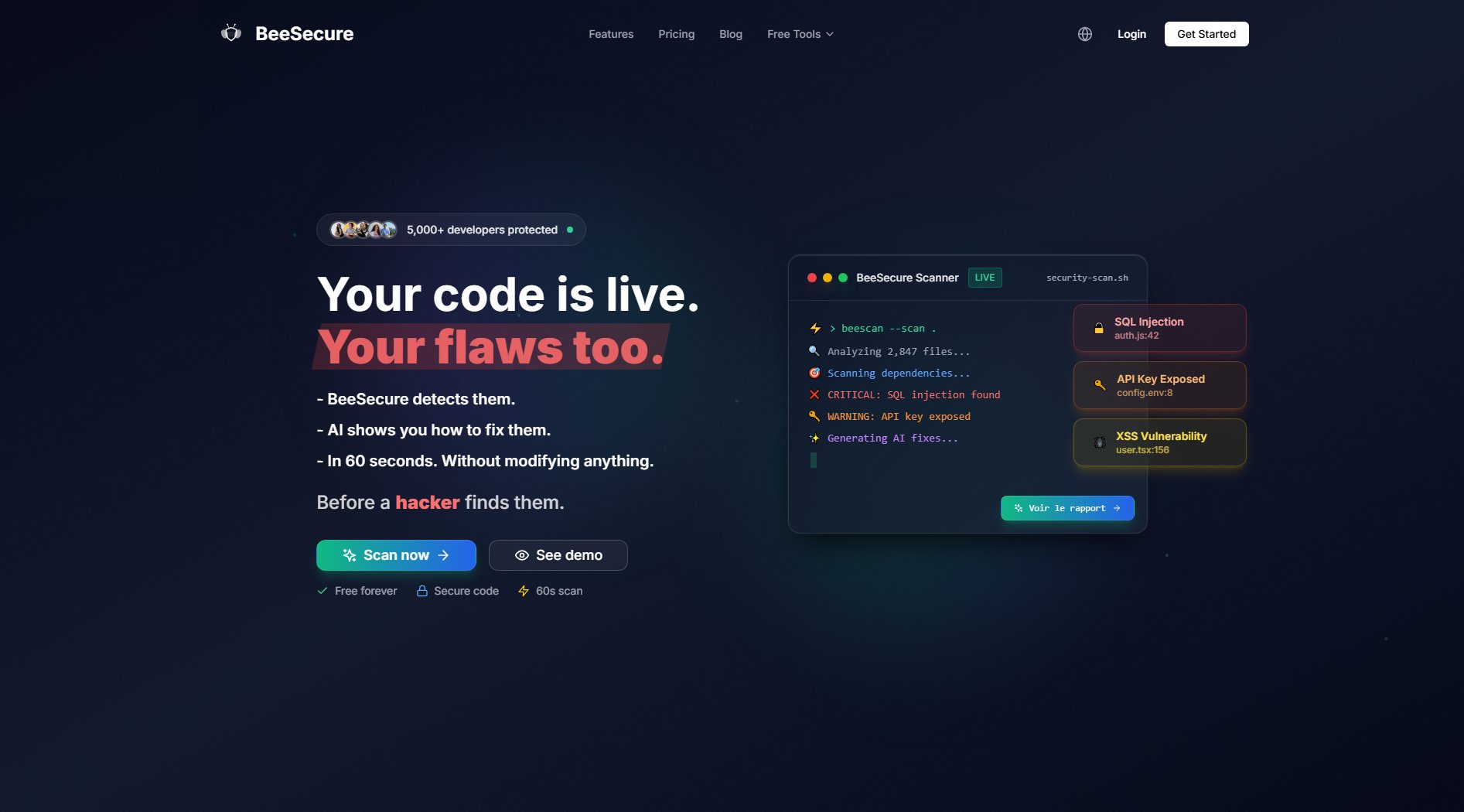
ThreatOps Interface & Screenshots
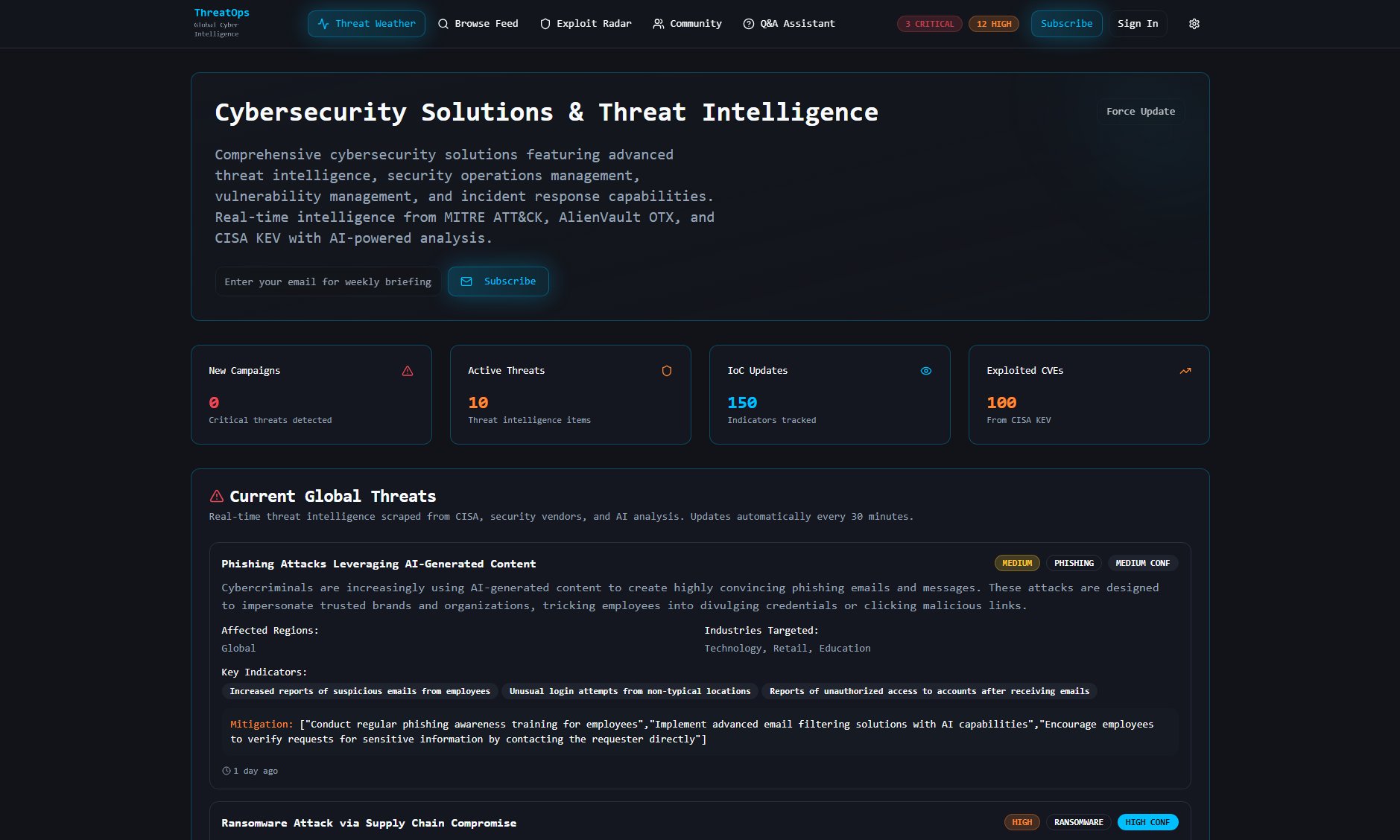
ThreatOps Official screenshot of the tool interface
What Can ThreatOps Do? Key Features
Real-time Threat Intelligence
ThreatOps provides continuously updated threat intelligence from multiple trusted sources including CISA, security vendors, and proprietary AI analysis. The platform tracks active threats, indicators of compromise, and exploited vulnerabilities with severity ratings and confidence levels.
AI-Powered Threat Analysis
Leveraging artificial intelligence, ThreatOps analyzes patterns across global threat data to identify emerging campaigns, predict attack vectors, and provide proactive defense recommendations. The AI engine correlates indicators across multiple sources to detect sophisticated attack patterns.
Comprehensive Threat Library
The platform maintains an extensive database of historical threats with detailed technical analysis, including malware signatures, attack vectors, affected systems, and mitigation strategies. Users can search and filter threats by type, severity, region, and industry.
Actionable Indicators of Compromise
Each threat includes specific IoCs such as malicious IPs, domains, file hashes, and behavioral patterns that security teams can immediately implement in their monitoring systems. The platform provides context around each indicator to help prioritize response efforts.
Targeted Mitigation Strategies
For each identified threat, ThreatOps provides detailed mitigation recommendations tailored to different organizational roles. These include technical controls, policy updates, user training points, and detection rules that can be directly implemented in security operations.
Best ThreatOps Use Cases & Applications
Enterprise Threat Monitoring
Security operations centers use ThreatOps to monitor emerging threats relevant to their industry, automatically importing IoCs into their SIEM systems to detect potential breaches early.
Incident Response
During security incidents, teams leverage ThreatOps to quickly identify if observed indicators match known threat actor tactics, techniques, and procedures (TTPs), accelerating investigation and containment.
Vulnerability Management
IT teams prioritize patching efforts based on ThreatOps intelligence about actively exploited vulnerabilities, focusing resources on the most critical risks to their environment.
Security Awareness Training
Organizations use ThreatOps data to develop targeted training materials highlighting current phishing campaigns and social engineering tactics relevant to their employee base.
How to Use ThreatOps: Step-by-Step Guide
Sign up for a ThreatOps account and log in to the dashboard. The platform offers both free and paid subscription options with varying levels of access to threat intelligence.
Configure your threat feed preferences by selecting relevant industries, regions, and threat types. The platform allows customization of alert thresholds based on severity and confidence levels.
Browse the real-time threat dashboard showing active campaigns, malware trends, and vulnerability exploits. Drill down into specific threats to view detailed technical analysis and indicators.
Export relevant indicators of compromise (IoCs) in various formats for integration with your SIEM, firewall, or endpoint protection systems. The platform supports STIX/TAXII for automated feed integration.
Implement recommended mitigation strategies from the platform's detailed threat reports. These may include technical controls, policy updates, or user awareness training specific to identified threats.
ThreatOps Pros and Cons: Honest Review
Pros
Considerations
Is ThreatOps Worth It? FAQ & Reviews
ThreatOps aggregates data from multiple trusted sources including CISA KEV, AlienVault OTX, MITRE ATT&CK, and proprietary AI analysis of global threat activity. The platform correlates indicators across these sources to provide comprehensive coverage.
The platform automatically updates its threat intelligence every 30 minutes, ensuring users have access to the most current information about emerging cyber threats and campaigns.
Yes, ThreatOps provides API access (in paid plans) and supports STIX/TAXII formats for integration with SIEM systems, firewalls, and endpoint protection platforms. Indicators can also be exported in common formats for manual implementation.
The platform covers threats across all major industries including technology, finance, healthcare, manufacturing, education, and government. Users can filter threats by industry relevance to focus on their specific sector.
ThreatOps' AI engine identifies patterns across disparate threat data points, detects emerging campaigns earlier than traditional methods, and provides predictive insights about likely attack vectors based on current trends.