Aikido
All-in-one security platform for code & cloud
What is Aikido? Complete Overview
Aikido is a comprehensive security platform designed to protect your code and cloud infrastructure. It combines multiple security scanning tools into one unified platform, reducing noise and false positives while providing actionable insights. Aikido helps developers and security teams identify and fix vulnerabilities quickly, ensuring secure deployments without slowing down development workflows. The platform is trusted by over 25,000 organizations and loved by 100,000+ developers for its ease of use, affordability, and effectiveness. Aikido supports a wide range of security needs, including static code analysis, dependency scanning, secrets detection, cloud posture management, and more.
Aikido Interface & Screenshots
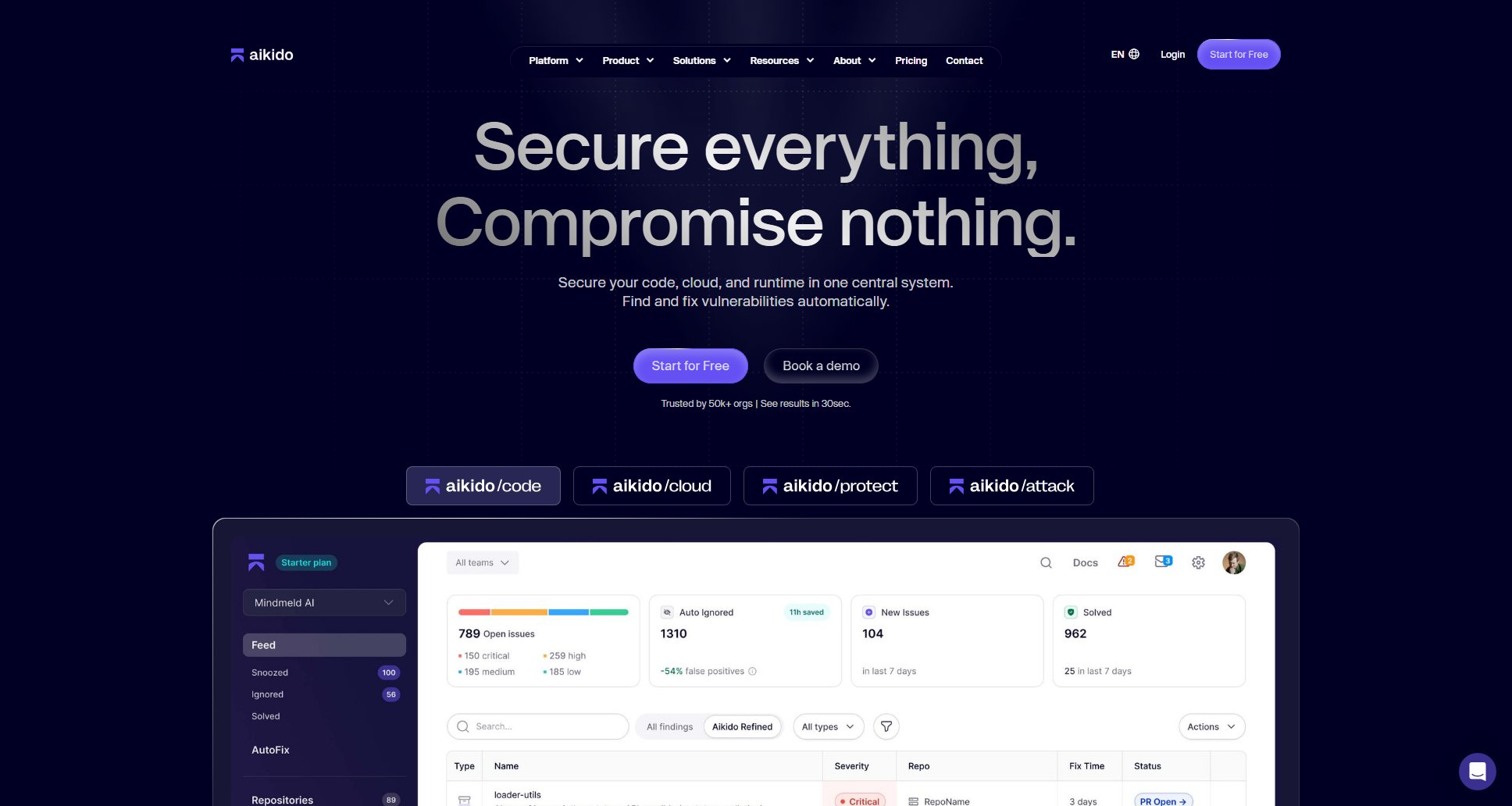
Aikido Official screenshot of the tool interface
What Can Aikido Do? Key Features
Open Source Dependency Scanning (SCA)
Aikido scans your open-source dependencies for known vulnerabilities, outdated packages, and license risks. It helps you stay compliant and secure by identifying problematic dependencies before they become a threat.
Cloud Posture Management (CSPM)
Continuously monitor your cloud infrastructure for misconfigurations, exposures, and policy violations across AWS, Azure, GCP, and other providers. Aikido provides actionable insights to fix issues fast.
Static Code Analysis (SAST)
Scan your source code for security risks before merging. Aikido's SAST tool identifies vulnerabilities like SQL injection, XSS, and more, helping you catch issues early in the development cycle.
Secrets Detection
Aikido checks your code for leaked API keys, passwords, certificates, and other sensitive information. It helps prevent accidental exposure of secrets that could compromise your security.
Infrastructure as Code Scanning (IaC)
Scan Terraform, CloudFormation, and Kubernetes configurations for misconfigurations. Aikido ensures your infrastructure deployments are secure by design.
Container Image Scanning
Aikido scans container images for vulnerable packages and outdated runtimes, helping you secure your containerized applications before deployment.
Runtime Protection
Zen, Aikido's in-app firewall, blocks critical injection attacks and introduces API rate limiting. It provides runtime security without disrupting your application's performance.
AI Autofix
Aikido's AI-powered autofix suggests and implements fixes for vulnerabilities directly in your IDE or CI/CD pipeline, saving developers time and effort.
Best Aikido Use Cases & Applications
Secure CI/CD Pipelines
Integrate Aikido into your CI/CD pipeline to automatically scan code and infrastructure before deployment. This ensures that vulnerabilities are caught early, reducing the risk of security breaches in production.
Developer-First Security
Aikido's IDE plugins allow developers to fix security issues as they code, reducing the backlog of vulnerabilities and making security a seamless part of the development process.
Cloud Security Posture Management
Use Aikido to continuously monitor and secure your cloud environments, ensuring compliance with best practices and preventing misconfigurations that could lead to data breaches.
Open Source Risk Management
Aikido helps organizations manage the risks associated with open-source dependencies by identifying vulnerabilities, outdated packages, and license issues in real-time.
How to Use Aikido: Step-by-Step Guide
Sign up for Aikido and connect your Git repository or cloud provider. No credit card is required to start.
Configure your scanning preferences, such as which repositories or cloud resources to monitor and the types of scans to perform.
Aikido automatically scans your code and infrastructure, identifying vulnerabilities and misconfigurations in real-time.
Review the findings in Aikido's dashboard, which prioritizes issues based on severity and relevance to your environment.
Use Aikido's autofix feature or follow the provided remediation steps to address vulnerabilities quickly.
Integrate Aikido with your CI/CD pipeline, IDE, or task management tools to streamline security workflows and ensure continuous protection.
Aikido Pros and Cons: Honest Review
Pros
Considerations
Is Aikido Worth It? FAQ & Reviews
Aikido combines multiple security tools into one platform, reducing noise and false positives by contextualizing vulnerabilities. It’s designed to be developer-friendly and integrates seamlessly with existing workflows.
No, Aikido guarantees read-only access to your codebase. It identifies vulnerabilities but does not make changes without your approval.
Aikido clones repositories into temporary environments (like Docker containers) that are disposed of after analysis. Your data is never stored permanently.
Yes, you can sign up and use a demo repository to test Aikido’s features without granting access to your actual code.
Aikido supports Visual Studio Code, JetBrains IDEs, Cursor, and Windsurf, with more IDEs being added regularly.