CPF - Cybersecurity Psychology Framework
Psychological vulnerability framework for cybersecurity professionals
What is CPF - Cybersecurity Psychology Framework? Complete Overview
The Cybersecurity Psychology Framework (CPF) is a comprehensive system that identifies and categorizes psychological vulnerabilities in cybersecurity contexts. It organizes human vulnerabilities into 10 primary categories, each containing 10 specific indicators mapped to established psychological research. The framework helps security professionals understand, anticipate, and mitigate human-factor vulnerabilities that attackers often exploit. CPF integrates decades of psychological research from authorities like Milgram, Kahneman & Tversky, and Cialdini into practical cybersecurity applications. The target audience includes cybersecurity professionals, organizational leaders, behavioral analysts, and anyone responsible for designing security systems that account for human behavior.
CPF - Cybersecurity Psychology Framework Interface & Screenshots
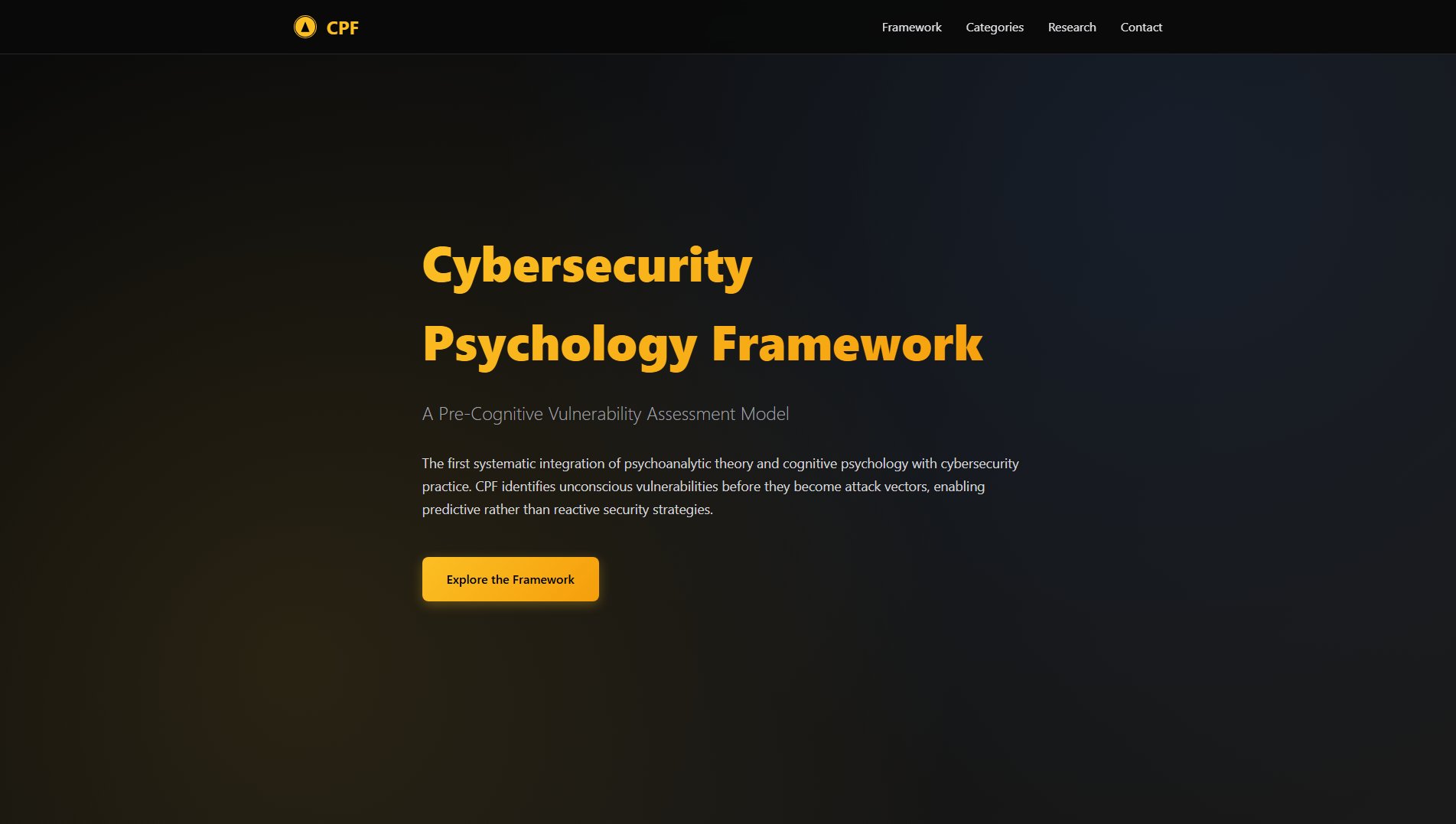
CPF - Cybersecurity Psychology Framework Official screenshot of the tool interface
What Can CPF - Cybersecurity Psychology Framework Do? Key Features
Authority-Based Vulnerabilities
Identifies 10 specific vulnerabilities related to obedience to authority figures and hierarchical structures, based on Milgram's research. Includes patterns like unquestioning compliance, diffusion of responsibility, and executive exception normalization that create security gaps in organizational contexts.
Temporal Vulnerabilities
Analyzes 10 time-related security vulnerabilities affecting decision-making quality, drawing from Kahneman & Tversky's work. Covers urgency-induced bypasses, time pressure degradation, and temporal exhaustion patterns that attackers systematically exploit.
Social Influence Vulnerabilities
Maps Cialdini's six principles of influence to cybersecurity contexts through 10 specific vulnerability indicators. Includes reciprocity exploitation, social proof manipulation, and scarcity-driven decisions that undermine security protocols.
Affective Vulnerabilities
Identifies 10 emotional and attachment-based vulnerabilities affecting security behaviors, based on Klein and Bowlby's research. Covers fear paralysis, anger-induced risk taking, and euphoria-induced carelessness that compromise security decisions.
Cognitive Overload Vulnerabilities
Details 10 vulnerabilities arising from cognitive limitations and information processing overload, building on Miller's research. Includes alert fatigue, decision errors, and complexity-induced mistakes that create security weak points.
Best CPF - Cybersecurity Psychology Framework Use Cases & Applications
Security Awareness Training
Use CPF to create more effective security awareness programs by targeting specific psychological vulnerabilities like authority-based compliance or social influence patterns that make employees susceptible to phishing.
Incident Response Planning
Incorporate stress response vulnerabilities into incident response plans to anticipate how team members might react under pressure and design protocols that account for these psychological factors.
System Design Review
Apply cognitive overload vulnerabilities when reviewing system interfaces to ensure security controls don't overwhelm users and thus get bypassed or ignored.
Red Team Exercises
Use the framework's categories to simulate more psychologically sophisticated attack scenarios during penetration testing and red team exercises.
How to Use CPF - Cybersecurity Psychology Framework: Step-by-Step Guide
Identify which of the 10 primary vulnerability categories are most relevant to your organizational context or security challenge.
Review the specific indicators within each category to understand potential psychological vulnerabilities in your systems.
Map these vulnerabilities to your existing security measures to identify potential gaps or weak points.
Develop targeted interventions, training, or system redesigns to mitigate the identified psychological vulnerabilities.
Regularly reassess using the framework to account for new threats and evolving psychological patterns in your organization.
CPF - Cybersecurity Psychology Framework Pros and Cons: Honest Review
Pros
Considerations
Is CPF - Cybersecurity Psychology Framework Worth It? FAQ & Reviews
CPF uniquely focuses on the psychological aspects of cybersecurity rather than technical vulnerabilities, providing a systematic way to understand how human behavior creates security risks.
The framework was developed by experts integrating decades of psychological research into practical cybersecurity applications, with credit given to foundational researchers in each category.
Yes, CPF complements technical security frameworks by addressing the human factors that technical controls often can't prevent, creating a more holistic security approach.
The website doesn't mention certification programs, suggesting the framework is currently primarily a research-based reference tool for professionals.
While the core categories appear stable, the inclusion of AI-specific vulnerabilities suggests the framework evolves to address emerging psychological aspects of new technologies.